AWS AgentCore’s September update makes agents enterprise native
AWS AgentCore just added VPC networking, PrivateLink, CloudFormation, and tagging on September 25, 2025. These controls move agents from demos to governed production. Learn how to design for security, cost, and scale.
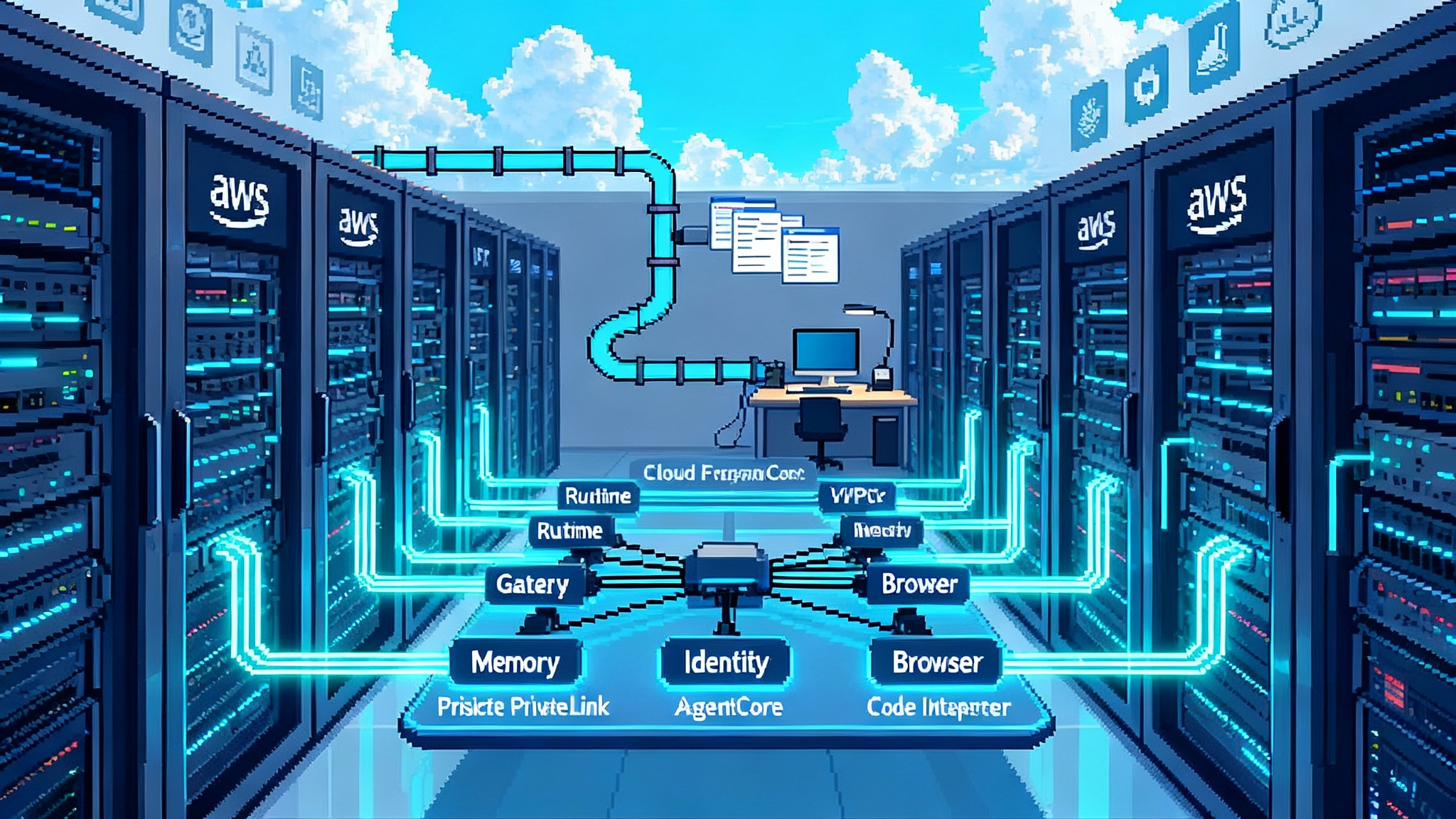
Breaking: agents just crossed the enterprise threshold
Ask any chief information security officer why agent pilots stall and you will hear the same list: private networking, identity controls, auditable operations, and predictable cost. On September 25, 2025, Amazon Web Services shipped updates that line up with those exact needs. The latest AgentCore release adds Amazon Virtual Private Cloud connectivity, AWS PrivateLink endpoints, AWS CloudFormation resources, and full resource tagging across Runtime, Browser, and Code Interpreter. For builders, it is the moment agents move from the expo floor to the change control board. If you want the official rundown, AWS details this update.
If you are building agent systems for finance, healthcare, or the public sector, this is the time to reframe your roadmap. Agents are not just applications with chat interfaces. With these September capabilities, they are becoming cloud primitives that plug into your existing policy stack the way a database or an event bus does.
From demo to data center: what enterprise native really means
Enterprise native does not mean a slick user interface. It means a service can live inside the security and operations scaffolding you already trust. Think back to early container adoption. Docker on a laptop was fun, but the real transformation came when orchestrators, virtual private clouds, and identity policies made containers schedulable, isolated, metered, and auditable. Agents are hitting that same crossover now.
Here is why the September upgrade matters:
- VPC networking places AgentCore traffic inside your private address space. You control routes, subnets, network access control lists, and monitoring. That unblocks workflows that touch systems that never traverse the public internet.
- AWS PrivateLink provides private connectivity to AgentCore services through interface endpoints so traffic stays on the AWS backbone. This meets strict egress rules and reduces attack surface.
- CloudFormation turns agents into infrastructure as code. You can template environments, run automated security scans on those templates, and promote changes through dev, test, and prod with the same rigor used for databases and queues.
- Tagging binds agents to your cost allocation, security boundaries, and governance. You can enforce attribute based access control, report costs by business unit, and sweep for orphaned resources.
Individually, these look like checkboxes. Together, they form the contract that lets you put agent workloads through architecture review without special pleading.
Quick refresher: what AgentCore includes
AgentCore emerged in July 2025 as a modular stack for agentic systems. The preview introduced a set of services that cover the lifecycle from tool wiring to runtime operations. If you missed that launch, start with the official AgentCore preview overview.
The key modules teams use most often:
- Runtime: Executes agents with isolation and autoscaling. Think of it as the cluster where agent sessions live.
- Browser: A managed, cloud hosted browser surface that agents can drive for tasks like form submission, scraping internal dashboards, or testing.
- Code Interpreter: A secure sandbox for executing agent generated code. Useful for data wrangling, simulation, and glue logic.
- Gateway: A registry and broker for tools so agents can call your internal APIs through a governed front door. It also speaks the Model Context Protocol, which eases tool standardization.
- Memory: Short and long term memory stores so agents preserve context responsibly without each team inventing its own store.
- Identity: Hooks into identity providers so you can map human users and agent roles to real credentials and policies.
- Observability: Event traces, metrics, and logs that help you debug and improve outcomes without reverse engineering a maze of prompts.
Many enterprises tested these pieces in a lab. The September update raises the ceiling for production.
Why VPC connectivity and PrivateLink change the risk math
Security leaders live by the maxim that the network is a boundary. With VPC support, AgentCore components can sit in your routable, private space. That means:
- Agents can call internal systems already inside your VPC. Market data services, claims adjudication engines, case management portals, and sensitive analytics clusters become reachable without punching holes through firewalls.
- You can apply your existing guardrails. Traffic flows through the network taps you monitor, the intrusion detection you run, and the packet mirroring you trust.
- You can write explicit path controls. For example, block all egress except PrivateLink to a defined set of AgentCore endpoints and allow calls only to six internal APIs through Gateway. That is a policy you can audit and prove.
For regulated teams, the open internet is where approvals go to die. Keeping agent traffic private removes entire classes of risk discussions. Instead of debating how safe something is, you can point to architecture patterns your organization already approves.
Infrastructure as code turns governance into muscle memory
Many agent pilots fail at the moment of scale. A clever team spins up an agent stack by hand. Then a second team asks for something similar. By the third request, you can no longer verify what is running, who owns it, or which environment is drifting.
CloudFormation lets you define agents, tools, policies, memory stores, logging, and network paths as code. Three practical wins follow:
- Repeatability: Spin up a new tenant or line of business by applying a versioned template that is already security reviewed.
- Change control: Use pull requests to propose changes to tool access or memory retention. Tests and policy as code checks run before anything reaches production.
- Drift detection: Detect and correct resources that slip out of compliance. If a sandbox interpreter was granted a larger quota during a crisis, you can ratchet it back with code.
Tagging ties this together. With consistent tags like cost center, data classification, owner, and environment, you can enforce permissions, automate cleanups, and allocate spend without chasing spreadsheets.
Open frameworks and MCP make agents portable
Most organizations will not bet everything on a single agent framework or model provider. Teams experiment with graph shaped workflows, multi agent orchestration, and retrieval centric tasks. AgentCore’s positioning is to meet those teams where they work. Runtime focuses on session isolation, scaling, and network posture rather than dictating how you compose agents. Gateway exposes tools via the Model Context Protocol so frameworks can discover and call them with minimal glue.
If your team is leaning into MCP, see how other stacks are moving. The piece on Boomi brings MCP to Agentstudio shows how vendors are standardizing tool contracts. For a parallel in managed runtimes, the Vertex AI Agent Engine leap highlights similar themes of isolation and governance. And if you are exploring browser controlled automations, the look at Comet background assistant explains why a managed browser surface matters for reliability and policy.
A helpful analogy is containers and orchestrators. Developers package apps in whatever language stack they prefer. The orchestrator schedules and isolates. With agents, frameworks handle plan and act patterns while AgentCore supplies governed compute, memory, identity, and observability that your platform team already understands.
A blueprint for production agents, sector by sector
Below is a practical, opinionated plan for shipping production agents in three heavily governed sectors. Use it as a checklist to accelerate architecture reviews and shorten the path from pilot to value.
Finance: post trade reconciliation and analytics co pilot
- Scope: An agent triages reconciliation breaks, enriches with market data, drafts journal entries, and raises tickets with suggested fixes.
- Network posture: Place Runtime in a VPC subnet with no public routes. Access AgentCore services through PrivateLink. Gateway exposes tools for internal trade books, market data, and ticketing. Deny all other egress.
- Identity: Map human users through your identity provider. Give the agent an execution role with scoped permissions to read only data and a break glass path to a limited write API behind a feature flag.
- Memory: Short term session memory expires within hours. Long term memory stores only de identified break patterns and remediation outcomes governed by your data retention policy.
- Observability: Emit traces to your centralized logging system, redact client identifiers at the edge, and capture decision artifacts for audit.
- Controls: All CloudFormation stacks must include tags for desk, product, and client classification. Run static analysis on templates to block internet egress and untagged resources.
- Cost guardrails: Set a per session token budget and hard concurrency caps. If the agent requests expensive tools like code execution, require an explicit plan approval step visible to the user.
- Failure playbook: If a tool fails, return a human readable incident note with a link to the trace. Escalate to the human owner when the same class of break repeats three times in a window.
Healthcare: prior authorization assistant for providers
- Scope: An agent compiles clinical summaries from the electronic health record, checks payer policy, drafts prior authorization forms, and schedules follow ups.
- Network posture: Keep all data flows inside the provider’s VPC. Use PrivateLink to reach AgentCore. Gateway publishes tools for electronic health record retrieval, payer policy queries, and scheduling systems.
- Identity: Enforce user to patient access through your identity provider and authorization service. The agent performs actions only in the context of a signed in clinician with appropriate role mapping.
- Memory: No patient identifiers in long term memory. Store only policy navigation breadcrumbs and de identified workflow templates. Rotate short term memory aggressively and encrypt everything at rest with customer managed keys.
- Observability: Capture a provenance log of every field auto filled or inferred. Make it exportable for compliance review.
- Controls: CloudFormation templates must include encryption by default, restricted subnets, and policy checks for minimum key lengths and allowed regions.
- Cost guardrails: Pre compute common policy lookups and cache results for hot specialties. Prefer retrieval calls over model tokens where possible. Alert when per visit costs breach thresholds.
- Failure playbook: If the agent cannot determine policy coverage with high confidence, it should produce a partial draft and label ambiguous fields for clinician review rather than guessing.
Public sector: permit processing triage
- Scope: An agent screens permit applications, validates attachments, checks zoning rules, and proposes an initial disposition for officer review.
- Network posture: Isolate Runtime in a government approved region and subnet. Use PrivateLink to reach AgentCore and the agency’s internal document repository. Block all public internet egress except approved allowlists for geospatial data if required.
- Identity: Integrate with the agency’s identity provider. Map agent actions to individual case officers for accountability. Use attribute based access control tags to ensure agents only touch cases in their jurisdiction.
- Memory: Persist only process templates and redaction rules. Case data stays in case management systems and is accessed at runtime through Gateway tools.
- Observability: Every decision must have a traceable plan and evidence bundle. Export weekly summaries for oversight committees.
- Controls: CloudFormation and tagging rules enforce environment separation, disaster recovery replication policies, and automatic key rotation. Require human in the loop checkpoints before any status change.
- Cost guardrails: Batch similar cases to reduce redundant reasoning. Move extract transform load steps out of the agent and into scheduled jobs that the agent triggers, so tokens are spent only on decisions.
- Failure playbook: If an external rule service is down, the agent pauses the queue and notifies the duty officer rather than guessing. Restart with backfill once the dependency is restored.
How to design for security, cost, and operations from day one
- Threat modeling: Treat every tool the agent can call as an entry point. List input and output schemas, expected side effects, and escalation paths.
- Data paths: Draw a data flow diagram of every hop the agent will take. Confirm that each hop stays inside VPC boundaries or private endpoints. Explicitly mark anything that would traverse the internet and replace it.
- Policy as code: Run security checks on CloudFormation templates before deployment. Block internet egress, enforce encryption with customer managed keys, and require mandatory tags.
- FinOps by design: Assign a cost owner tag. Set per environment budgets and alarms. Record model usage per feature and measure cost per successful outcome, not only per token.
- Drift response: Schedule drift detection on stacks. Any manual change triggers an incident. Roll the change back and open a pull request to capture it properly.
- Tool governance: Register tools through Gateway. Require owner tags, service level objectives, and a contact rotation. Unowned tools do not get endpoints.
- Observability norms: Require traces with input size, tool calls, latency, and outcome. Use these to tune prompts, tool ordering, and retrieval strategies. Feed real failure cases into a weekly improvement loop.
What this means for build versus buy
The September changes also fit into a larger market trend. There is rising interest in agent catalogs from vendors who list prebuilt assistants. Those catalogs are useful for discovery and trials. The missing piece has been reliable deployment inside your network with your controls. With AgentCore’s VPC, PrivateLink, CloudFormation, and tagging support, vendors can ship artifacts your platform team can deploy and govern like any other workload. The net effect is faster adoption without compromising policy.
If you build, these capabilities shorten the time from proof of concept to production by giving you network posture, infrastructure as code, and cost tagging out of the box. If you buy, they give you the levers to accept third party agents into your environment without bespoke exceptions.
The real risks and the honest caveats
- AgentCore remains in preview. Engineering leaders should weigh region coverage and support expectations before migrating critical paths.
- Browser and Code Interpreter are powerful tools, which also means a larger potential blast radius if misused. Limit their access to only the domains and data sets they need, and prefer read only modes where possible.
- Costs can spike during early iteration. Instrument every agent flow. When you find token heavy steps, replace them with cheaper deterministic tools or cached results.
- Observability is not optional. Without traces and metrics, debugging agents is guesswork. Make observability a hard gate for promotion to production.
The bottom line
With the September 25 update, AWS has made agents feel less like apps and more like building blocks. VPC networking and PrivateLink close the biggest security gap. CloudFormation and tagging bring agents under the same governance umbrellas you already trust. The preview era modules round out the runtime, tool access, code execution, memory, identity, and observability that real programs need. Open frameworks and the Model Context Protocol let you keep your cognitive layer portable while your platform team locks down the perimeter.
If you have been waiting for a crisp reason to move from pilots to production, this is the moment. Start with a single, bounded use case. Land the network posture and the infrastructure as code. Wire Gateway tools through MCP, set a cost budget, and light up observability. Then expand by cloning the template to the next line of business.
There is a narrow window when new capabilities allow early adopters to compound advantage. Agents are stepping out of the demo booth and into your change log. The organizations that treat them as infrastructure will write the next set of best practices.