Browser-native agents surge as Amazon sues Perplexity
Amazon’s lawsuit against Perplexity marks a tipping point for browser-native agents. The fight shifts from chat boxes to carts and checkout, forcing new norms for identity, consent, pacing, and standards on the open web.
The day the browser became the battleground
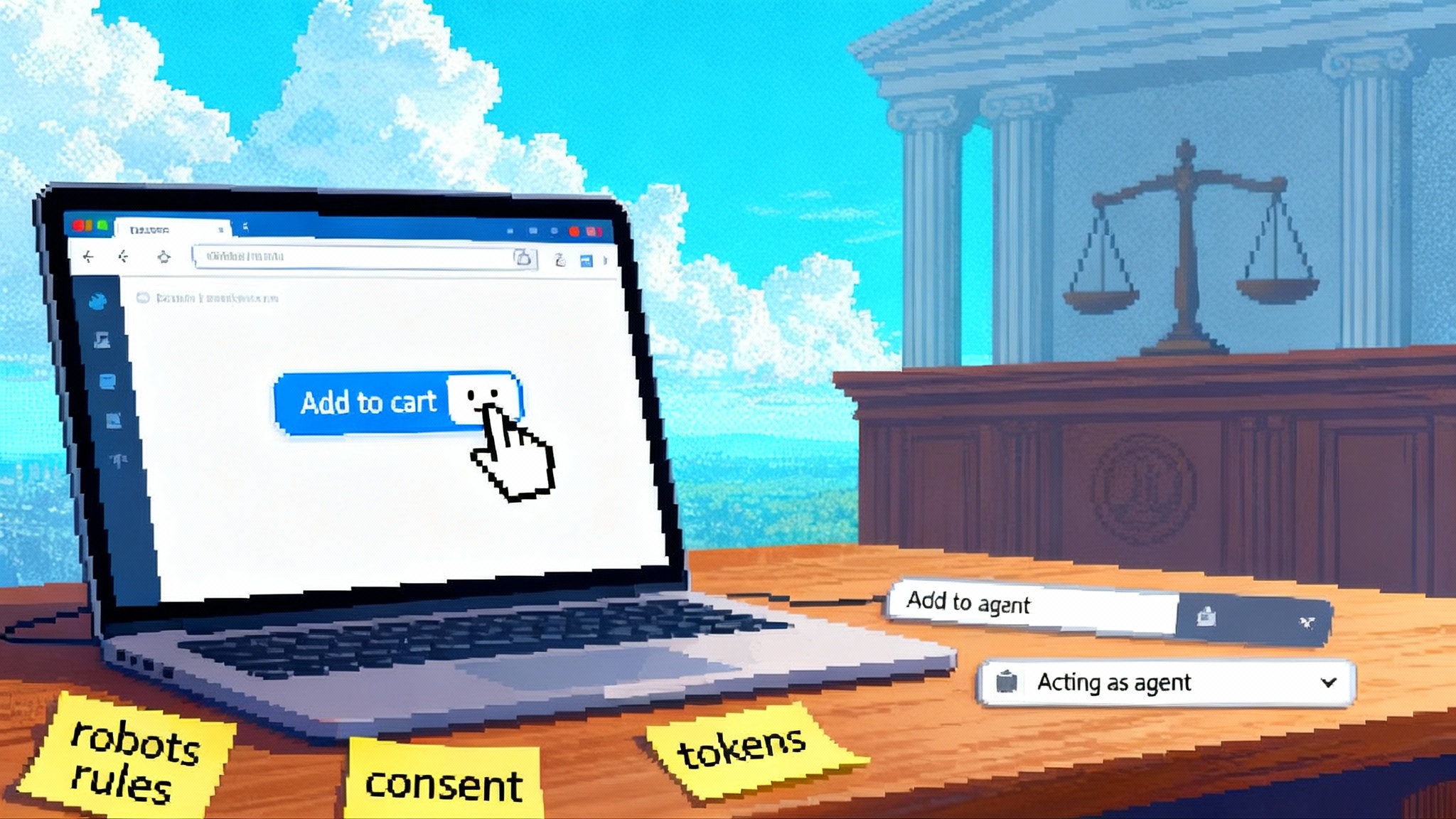
On November 4, 2025, Amazon filed a lawsuit accusing Perplexity of covert automated shopping through its Comet browser agent. The complaint alleges the agent posed as a human, accessed customer accounts, and degraded Amazon’s carefully tuned shopping experience. Perplexity denies wrongdoing and says credentials live on user devices, not on its servers. However this case resolves, it marks a clear transition point: agent software has moved from conversations to transactions. The front line is now clicks, carts, and checkout inside the browser, not just answers in a chat box. You can read the core claim in Reuters’ report that Amazon has filed a lawsuit accusing Perplexity.
Why now? Because Comet did not remain a niche experiment. After a summer pilot limited to premium subscribers, Perplexity flipped the switch in early October and made its agentic browser broadly accessible. That instantly changed the stakes for every platform that must decide whether a nonhuman user with permission from a human counts as a user at all.
From chat to clicks: why this case matters
The last two years were dominated by conversational answers. The next two years will be defined by action. Browser-native agents are moving from summarizing the web to operating on it. They enter passwords you approve, apply discount codes, compare delivery windows, and click the buy button. Think less of a chatbot and more of a capable intern with your keys, your instructions, and a short daily checklist.
Comet’s shift into the mainstream is the proof point. Perplexity’s browser was initially a premium perk. On October 2, 2025, it became a consumer product anyone could install. The Verge covered that pivot in detail and confirmed Comet is available to everyone for free. Once agents run beside tabs rather than inside chats, the boundary between regular browsing and automated action disappears for everyday users. That is a feature for consumers and a shock to platforms built around human traffic.
If you have been tracking the broader arc, this moment connects to earlier milestones. We explored how an operator-style paradigm can make assistants feel like software instead of conversation in agent goes mainstream as operator, and how consumer access changes expectations in consumer agent finally lands. Commerce raises the stakes because every click carries money, identity, and risk.
What Comet actually does, in plain terms
Here is a simple example. You tell the agent: Find a 14-cup food processor under 120 dollars, in stock this week, with parts you can replace. A human opens several tabs, skims specs, checks coupon sites, signs in to a store, looks at shipping fees, and finally buys. A browser-native agent can do that same flow at superhuman speed.
The difference is not magic. It is sequencing. The agent performs many small actions and stitches them together: fetch a page, interpret options, follow a link, add to cart, authenticate, apply a code, select shipping, confirm. The value comes from doing dozens of these actions across many merchants in a few minutes. That is why platforms care. Automation turns every site from a destination into a function call and makes comparison shopping less about loyalty and more about performance.
Where platforms draw the line
Most major sites welcome robots in some form, but on their terms. Crawlers identify themselves. Rate limits are respected. Site owners publish what is allowed and what is forbidden. Consumer sites add another layer, since accounts carry money, identity, and security risk.
Amazon’s complaint highlights two bright lines. First, do not pretend to be human if you are not. Detection systems and terms of service often require automated traffic to declare itself. Second, do not automate login and account actions in ways that bypass or weaken the protections a site relies on. If an agent logs in for a user, the platform wants confidence that the user approved it and that the agent will not hammer servers with frantic retries.
Treat these lines as product constraints, not legal footnotes. Practical guardrails will determine who survives. Agents that hide will be blocked. Agents that are legible can negotiate.
The norms to bake in now
When a technology wave meets platform rules, norms appear fast. Here are six that winning products should implement by default.
1) Agent identity the web can read
- Send a clear user agent string that names the agent, its version, and its runtime. Do not spoof a human browser or use a generic headless identifier.
- Add a dedicated header for intent, for example Agent-Intent: compare prices or Agent-Intent: purchase. This tells sites why the agent is present and lets them tailor responses. Start simple. Even a two-value vocabulary, browse versus purchase, is useful.
- Publish a machine readable page that documents the agent’s behavior. If you tell sites what you do, you can credibly ask for access.
2) Explicit consent with scopes, not blanket approval
- Borrow the idea behind authorization scopes, where a user grants specific permissions to a client application. Translate it to the open web. A site could ask for read listings or manage cart or place order scopes, each with its own prompts and timeouts.
- Add step up approval at sensitive moments. A biometric prompt on the device for the first purchase of a session, a read aloud confirmation of item and price, a visible countdown to cancel before placing an order.
- Show a simple receipt of what the agent did. Include pages visited, items added, codes applied, and the final price.
3) Rate limit aware design as a first class feature
- Give every domain a budget of actions per minute, hour, and day. Stop early, not late.
- Use backoff, randomness, and caching. If you misjudge capacity, back off quickly and try again later. Do not make a struggling server your problem.
- Make all this visible in product settings. Offer a gentle mode that acts slower and is less likely to get blocked.
4) Robots for agents, not just crawlers
- The web already uses a robots file to guide crawlers. Extend the idea. Support a simple agents file or an agents meta tag that can say allow browse, allow compare, require token for purchase, or disallow purchase.
- Respect human readable notices that say no automated checkout while you wait for a standard. Acting better than the minimum earns trust and case by case access even before a standard exists.
5) Token based handshakes that prove who is who
- Create an Agent Connect flow that lets a site issue a time bound token to your agent. Bind it to the device using a hardware backed key like the ones Web Authentication relies on. If the token is stolen, it will not work on a different machine.
- Use the token to mark sensitive actions such as add to cart or apply code. Sites can throttle or revoke tokens without banning users.
6) Audit trails and red teaming for the things that matter
- Log every action that changes money or identity. Let users export the log. Let sites request hashes of those logs during disputes.
- Red team your own agent. Try the attack a platform fears most. Simulate heavy shopping traffic and measure how your system backs off. Try to bypass your own consent gates and fix the gaps before someone else finds them.
A practical example: building a courteous shopper
Imagine you are shipping a new shopping workflow. You want superhuman speed without platform conflicts. Here is a minimal design that keeps you out of trouble and is easy to explain to users and partners.
- Identity: The agent sends a truthful user agent string and a simple intent header that flips from browse to purchase only when the user enters the confirmation screen.
- Consent: At purchase time, the agent shows a one screen summary that includes store name, item, quantity, price, shipping, and any codes to apply. The user approves with a fingerprint or a short passcode.
- Handshake: If the store supports agent tokens, the agent requests one after login. If not, it continues with conservative rate limits and displays a small banner saying acting as a guest agent.
- Pacing: Browsing is limited to a few actions per second with a soft cap of hundreds per hour per store. Purchases are one every thirty seconds with a visible spinner that explains why.
- Memory: Credentials never leave the device’s keychain. Tokens are bound to that device. Shopping sessions expire after an hour of inactivity.
- Trail: A receipt shows every click. Users can share that receipt with support if anything goes wrong.
If this sounds slower than a headless script, that is the point. You are buying long term access at the cost of a little speed. People prefer a reliable assistant over a fast one that gets locked out.
The distribution squeeze is real
Messaging channels once looked like a distribution shortcut for assistants. That window is narrowing as major platforms tighten automation policies in customer chat interfaces. Agents will need the browser even more. It is the channel that nobody owns, but it is also the channel where every site can raise defenses if it sees anonymous automation.
This tension explains the stakes of Amazon versus Perplexity. Commerce platforms do not want unidentifiable agents wandering the aisles. Agent builders want user authorized help that actually helps, which often means acting in ways sites did not design for. There is a compromise if both sides can see who is acting, what they are doing, and how frequently they do it.
What this means for shoppers and researchers
If the browser becomes a place where trustworthy agents act openly, shoppers will get real benefits:
- Better comparisons. Agents can check stock, shipping, and return policies across many stores quickly.
- Less time wasted. You can hand off the part most people dislike, which is retyping addresses, rechecking sizes, and looking for codes that might not work.
- Safer habits. A good agent will nudge you toward two factor prompts and away from sketchy checkout pages.
For researchers and knowledge workers, the same principles apply. Agents that declare themselves and pace their work will keep access to the news sites, archives, and databases they rely on. Agents that hide will be throttled, and their users will feel the pain.
If you are building enterprise agents, note how these consumer norms rhyme with what we covered when AWS turned AgentOps into a cloud primitive. Identity, policy, and observability do not just prevent abuse. They unlock higher trust use cases and better partnerships.
Expect a standards scramble
Every platform era eventually writes standards. That will happen here too. In the next twelve months, watch for:
- Agent specific user agent conventions, agreed by major browser vendors and model providers.
- A simple allow list format for actions, starting as a community draft and later moving into a formal standards track process.
- A reference design for agent tokens that reuses proven building blocks like public key cryptography and device bound credentials.
- A best practices guide that turns consent from a legal block of text into clear, timed prompts that match the risk of the action.
If you build agents, you can help by publishing your early approach so others can critique it. If you run a platform, you can help by describing the behaviors you can support and the ones you will block. Clarity helps both sides and reduces the temptation to sneak.
How incumbents will respond
Expect the familiar playbook. Platforms will use more sophisticated bot detection at the edge. They will challenge suspicious sessions with stronger identity checks. They will introduce first party agents and describe them as safer. They will strike bilateral deals for tokens that allow higher limits in exchange for direct accountability.
That might sound like a moat, but it is also an offer. If independent agents accept identity, consent, and pacing, they can earn a durable place. If they push past the lines, they will end up fighting a technical and legal cold war that burns time and money.
The next 60 days: a builder’s checklist
- Publish your agent identity and intent policy. Make it short, make it clear, and ship it with a version number.
- Add purchase scopes and step up prompts. Give users a visible, reversible checkpoint before money moves.
- Implement domain budgets and exponential backoff. Start conservative and let users opt into faster modes later.
- Store credentials locally using the system keychain. Never collect passwords on your servers.
- Add a receipt style activity log for sensitive actions.
- Reach out to the top ten sites your users frequent. Offer to test agent tokens and to honor any published agent rules.
- Build a kill switch that disables automated checkout if a partner asks or if your monitors see elevated block rates.
None of this requires new standards to exist. It requires taste, restraint, and a willingness to trade a little speed for a lot of trust. Your product will feel more professional on day one, and you will not need to rewrite it after the first platform confrontation.
What the court can decide, and what the market will decide
Courts can set boundaries for unauthorized access, contract enforcement, and deception. They can clarify whether an agent with a user’s blessing is a user in the eyes of the law when it takes sensitive actions. They can define what counts as misrepresentation when software looks human. Those rulings will matter.
The market will still decide how most agents work. If shoppers trust clear consent flows, if researchers trust agent identity, if platforms see respectful pacing, then the web will adjust to automated help. If not, the browser will become a patchwork of walls and secret handshakes, and only a few players will have the keys.
Conclusion: earn the right to click
The browser is not just a document viewer anymore. It is the operating system for agent work. Comet’s public arrival and Amazon’s lawsuit make that change impossible to ignore. If you are building agents, the path forward is simple to say and hard to do. Be honest about who you are. Ask before you act. Move at a pace partners can live with. Ship the proof of these choices into your product so users and sites can see it.
Do this and you will still deliver superhuman shopping and research. You will do it in a way that stands up in courtrooms and integration meetings. The browser rewards software that behaves. That is how you win this new market and keep access while everyone else is still arguing about it.