Agent Control Towers Arrive: Covasant and OutSystems Lead
Two enterprise launches turned agent ops from slideware into shipped software. Covasant introduced a governance control tower and OutSystems brought Agent Workbench to general availability, signaling a real control plane for AI agents.

The week agent ops became real
On September 4, 2025, Covasant announced its AI Agent Control Tower, positioning it as a command center for governing, observing, and securing fleets of enterprise agents. The company’s message was blunt and practical: agents are multiplying, costs are rising, and visibility is thin. A control tower adds radar, rules, and routes, so teams can operate at scale without losing safety or cost control. See the official details in the Covasant control tower release.
Only days later, on October 1, 2025, OutSystems used its One Conference stage in Lisbon to take Agent Workbench to general availability, giving development and operations teams a low code way to design, orchestrate, and supervise agents inside real workflows. The product moved from early access to a supported release that emphasizes governance, security, integration, and support for the Model Context Protocol. You can confirm the milestone in the OutSystems GA announcement.
Put these moments together and the signal is clear. The control plane for agents is arriving, not in slide decks, but in shipped software. This is the start of agent operations as a discipline, similar to how containers forced the world to invent Kubernetes. Agents are autonomous microservices that can read, plan, and act. Without a control plane, teams are managing them with sticky notes and hope.
Why control towers matter now
If your organization has even a handful of agents reading contracts, reconciling invoices, negotiating delivery dates, triaging support tickets, or drafting compliance memos, you already feel the pressure. Each agent has tools, data permissions, and operating rules. Multiply that across business units and the risk compounds. A control tower creates a shared brain and shared brakes, so autonomy does not become anarchy.
The difference between a dashboard and a control tower is authority. A dashboard describes. A control tower can direct. In practice, that means the ability to stop, quarantine, reroute, and enforce policy across heterogeneous agent platforms. Authority is the missing ingredient when autonomous software touches money, data, and customers.
What an agent control tower actually does
Let’s make it concrete. A credible control tower should provide at least these capabilities:
- Agent registry and identity: a single catalog of every agent, who owns it, what version it runs, what tools it can call, and which data it is allowed to touch. Treat agents as first class identities, not headless scripts.
- Policy and guardrails: centrally define what an agent can do and under what conditions. For example, a finance agent may propose journal entries automatically, but must request human approval above a spend threshold.
- Telemetry and cost visibility: measure tokens, calls, time to completion, tool latencies, and error rates by agent and by workflow. Cost accountability is how you stop budget leaks.
- Observability and traceability: capture each decision path, tool call, and data access so audit and debugging are normal operations, not special events.
- Incident containment: pause or quarantine an agent that misbehaves, roll back to a safe policy bundle, and notify the owner without taking down the whole system.
When these features exist in one place and are applied consistently, security teams can sleep, finance teams can forecast, and product teams can move faster with less fear of unintended consequences.
Why this is happening in late 2025
Three forces converged this year:
- Agent sprawl got real. Teams shipped dozens of narrow agents for tickets, emails, and forms. The cumulative surface area became a risk, not a curiosity.
- Interoperability matured. The Model Context Protocol gave agents and tools a shared vocabulary, making cross vendor control practical instead of aspirational.
- The first meaningful scare. In late September, security researchers documented a malicious Model Context Protocol server hiding in a trojanized package that silently blind copied outbound email. It was not sophisticated, but it was enough to prove the point. If you let agents plug in servers without identity, signing, and provenance, you invite supply chain surprises.
Adoption drives standardization. Standardization attracts platforms and attackers. Governance grows up in response. We have seen this movie with containers, mobile device management, and SaaS identity.
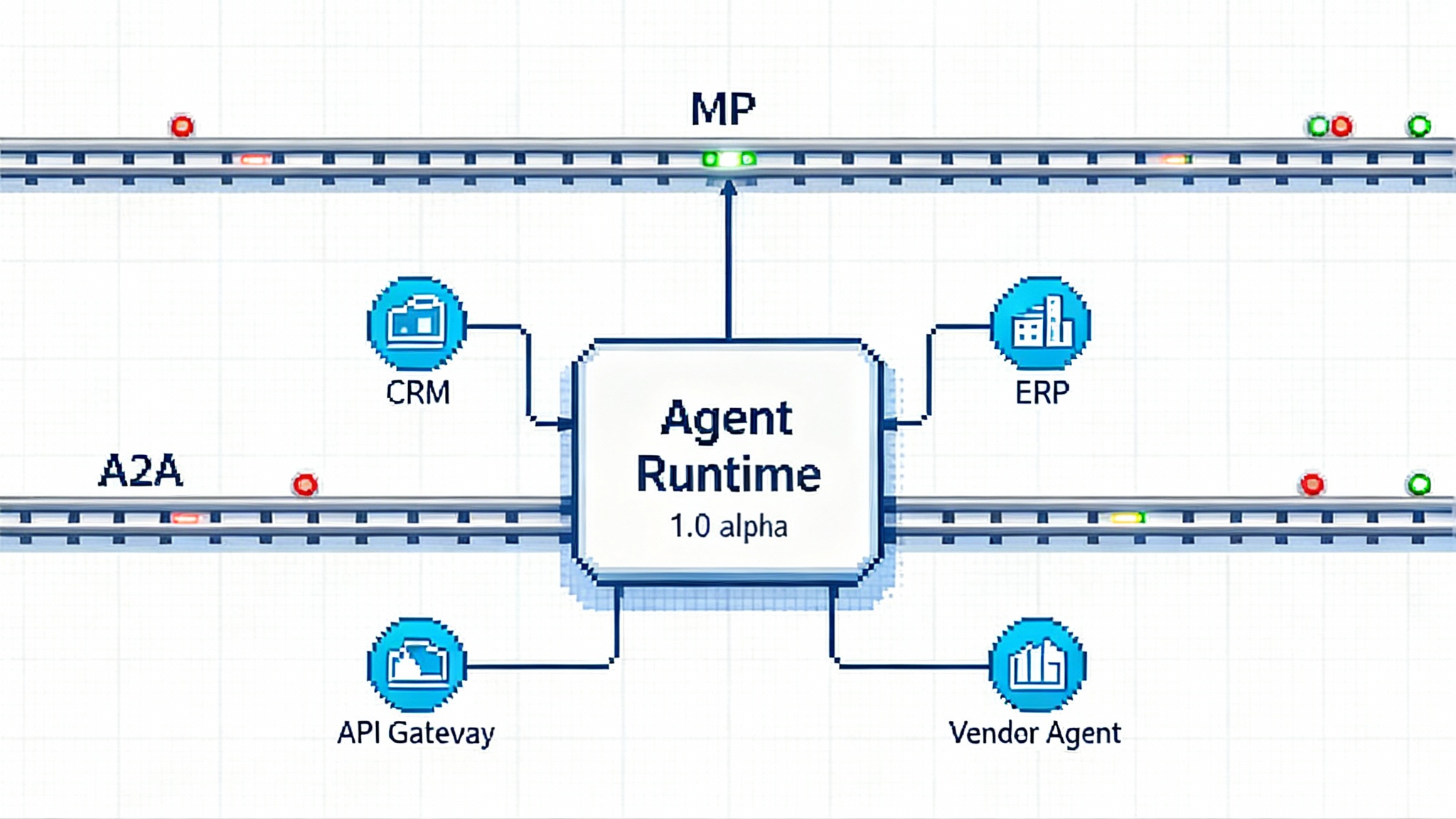
The emerging architecture for agent ops
Picture a three tier stack that separates execution from governance:
-
Data and tools: email, contracts, enterprise resource planning, customer relationship management, data warehouses, retrieval pipelines, and proprietary services.
-
Agent execution layer: planners, reasoners, and workers that call tools, read data, and perform tasks. These may run inside platforms like OutSystems Agent Workbench, inside cloud providers, or on your own infrastructure.
-
Control plane: a product like Covasant’s control tower or a set of homegrown services that handle identity, policy, audit, observability, incident response, and cost management across all agents and platforms.
Standards fit across the layers. Model Context Protocol defines how agents and servers talk. Identity frameworks such as OpenID Connect and System for Cross domain Identity Management define how agents are issued credentials and how those credentials are enrolled and revoked. Telemetry should be agent aware, not only model aware, using structured events, distributed traces, and cost meters that include task context.
A useful design choice is to separate where agents execute from where they are governed. You might execute a pricing agent inside a low code platform for speed, but govern all agents centrally for safety and finance. That separation made cloud possible. It will make agents usable at scale.
For a security deep dive that complements this architecture, see our take on agent native security for enterprise AI. For a view on value measurement, consider how proactive BI agents are here and what that implies for metrics you can trust. And for ecosystem rails that enable commerce and interoperability, see the early shape of open rails for agent commerce.
The supply chain is now part of agent security
The September incident was small in code and large in implications. It highlighted two truths:
- Agents are granted high trust. A simple server plugin can inherit read and write access to sensitive systems like email, tickets, and databases.
- Many organizations do not version pin, verify signatures, or maintain allowlists for Model Context Protocol servers. What is standard practice for container images often does not exist for agent connectors.
The answer is not to ban agents. It is to treat them like production software with supply chain controls. If a server or connector can act with the authority of a person or a system account, it must be onboarded through the same gates you use for any privileged component.
Practical measures include signed releases, software bills of materials for external components, hash pinning for connectors, and a living allowlist with owners and review cadences. These do not slow you down when they are automated. They do stop the easy attacks.
A 90 day playbook for startups building do work agents
The next quarter can be the difference between a promising demo and a production ready agent business. Here is a plan that balances speed, safety, and proof of value.
Days 0 to 30: Interoperability and identity groundwork
- Adopt the Model Context Protocol for all tool connections. If you already use it, freeze on a known good version and add a change control process. That buys portability across platforms and clients.
- Define agent identity on day one. Issue each agent a unique identity and short lived credentials. Use OpenID Connect for authentication and System for Cross domain Identity Management for lifecycle management when possible. If that is heavy for your stage, implement per agent service accounts with rotation.
- Build an agent registry. It does not need to be fancy. A metadata table with agent name, owner, version, scopes, and last activity is enough to start. Make owners real people and make the registry visible to your team.
- Version pin and sign critical components. Require a software bill of materials for any server or connector you did not write. Store known good hashes and refuse to run unknown builds in production.
- Choose your control plane path. You have two options. Integrate with a product like Covasant’s control tower to get policy and observability quickly, or scaffold the basics yourself with a roadmap to adopt a product later.
Interoperability checklist
- Support Model Context Protocol servers and clients across at least two execution environments.
- Provide webhook style callbacks and event streams so the control plane can observe agent steps in real time.
- Expose a standard policy hook. Before an agent executes a high risk tool, call a policy service that can allow, deny, or require approval.
- Emit structured telemetry per step with task identifiers, tool names, decision summaries, token counts, and durations.
Days 31 to 60: Governance hooks and safety engineering
- Human in the loop controls. Implement explicit approval for high risk actions. Start with three categories: money movement, data egress, and customer communications. Approvals can be lightweight. A queue with two person confirmation is enough.
- Policy bundles. Write machine enforceable rules. Examples: never email outside allowlisted domains, never exfiltrate customer data without masking, never hit a production system with a write method unless a change window flag is present.
- Incident drills. Simulate a bad server or runaway agent. Practice quarantine, rollback, and credential rotation. Time them and treat them like site reliability drills.
- Secure the supply chain. Maintain an allowlist of approved Model Context Protocol servers and pin versions or hashes. Require signed releases. Add anomaly detection for patterns like silent blind copies, unexpected domains, or sudden spikes in egress traffic.
- Establish agent cost budgets. Give each agent a monthly budget for tokens or calls. Alert at 50 percent, 80 percent, and 100 percent thresholds and automatically degrade to a safe mode when limits are reached.
Governance hooks to implement
- Pre execution policy check and post execution audit event
- Real time kill switch per agent and per policy bundle
- Owner notification on policy violations and cost overruns
- Evidence logging that captures prompts, tool calls, and outputs without exposing secrets
Days 61 to 90: Metrics that prove return on investment
Pick a small set of outcome metrics and instrument them so they emit automatically. Focus on speed, quality, and cost:
- Cycle time per task before and after agent adoption
- Percent of tasks completed without human intervention for a stable class of work
- Error and rework rates, including guardrail violation counts
- Mean time to recovery when an agent is paused or rolled back
- Cost per completed task including model calls and infrastructure
- Customer or employee satisfaction deltas when agents touch people
Create a lightweight value tracker that pairs savings and quality gains with costs per agent. This avoids hand waving in board updates and helps your customers buy with confidence.
Build versus buy for the control plane
Startups often default to building everything. That does not scale when your customers want governance and audits on day one. Use this pragmatic map.
When to integrate with a control tower product
- You plan to sell into regulated or procurement heavy accounts in the next six months.
- You expect to support multiple agent platforms and cloud regions.
- Your core value is a domain agent, not the governance plumbing.
- You lack a dedicated team for policy, identity, and observability.
What to do: Pilot a commercial control tower with two or three of your highest value agents. Integrate policy hooks, telemetry, and identity. Measure setup effort, time to approval, and incident handling. If the product pays for itself in reduced risk and faster sales cycles, standardize on it. Integrate your registry so the product becomes your source of truth.
When to build core pieces yourself
- You sell to a narrow segment with uniform infrastructure where a minimal governance layer is sufficient.
- Your agents require custom policies that a generic product cannot express yet.
- You need unique telemetry that ties deeply into your own runtime.
What to do: Build a lean control plane that covers the basics. Implement an agent registry, a policy service with human approval, a telemetry stream, and a kill switch. Use standards so you can plug into a commercial product later without rework. Keep the code small and auditable. Avoid cleverness. Every line you do not need is a future incident you do not have.
The likely hybrid reality
Most teams will mix. Use a platform like OutSystems for execution when you want speed and built in integration with identity and governance features. Pair it with a control tower that sees across platforms so your security and finance teams have one place to govern. Keep a thin layer of homegrown code where your differentiation lives.
Contract and procurement tips for agent ops
If you buy a control tower, negotiate for:
- Clear model and data boundaries. Who runs the models, who holds the prompts, and how data is isolated by tenant.
- Evidence export. You must be able to export audit logs, traces, and costs in open formats.
- Policy as code. You want predictable, versioned policies that can be peer reviewed.
- Identity integration. Support for enterprise identity providers and a clear story for agent identities that are not tied to people.
- Response time commitments for security issues and a published incident response process.
If you build, commit to:
- Security reviews before releases, especially for server integrations
- Version pinning and signed builds for connectors
- Regular rotation of agent credentials and keys
- Lightweight red team exercises that test prompt injection, output handling, and server impersonation
Early wins that close deals
Buyers care about outcomes and risk. Show both:
- Return on investment: reduce cycle time on a named workflow by a specific percent within 30 days. Publish the before and after.
- Safety and compliance: demonstrate policy enforcement with evidence logs on a realistic scenario. Show who approved what and when.
- Cost control: present per agent cost curves with budgets and alerts. Show an automatic degrade to safe mode when spending spikes.
- Reliability: run a planned rollback during a demo and recover an agent to a previous policy bundle in seconds.
What this means for founders and platforms
The pattern is set. Covasant’s launch gave the governance story a home. OutSystems’ release showed that orchestration is becoming a feature of mainstream platforms, not a research project. Standards like Model Context Protocol will widen the ecosystem and, as the recent incident proved, will attract attackers who prefer misconfigurations over exploits.
If you are building do work agents, decide now where your control plane lives. Integrate with one, build a minimal one, or blend both. Give every agent an identity. Add policy hooks from the start. Prove value with metrics, not adjectives. Treat servers and connectors like production software with a supply chain. When a customer asks how you will govern a fleet of agents at scale, answer with a demo, a dashboard, and a playbook, not a promise.
The sky is filling with traffic. The lights in the control tower are coming on. The teams that ship with governance built in will land the biggest deals.