Cloudflare Remote MCP makes the edge home for AI agents
Cloudflare’s remote MCP servers move AI agents off laptops and into a global edge with identity, per-user state, and durable execution. Learn how to migrate to production with strong guardrails, observability, and speed.
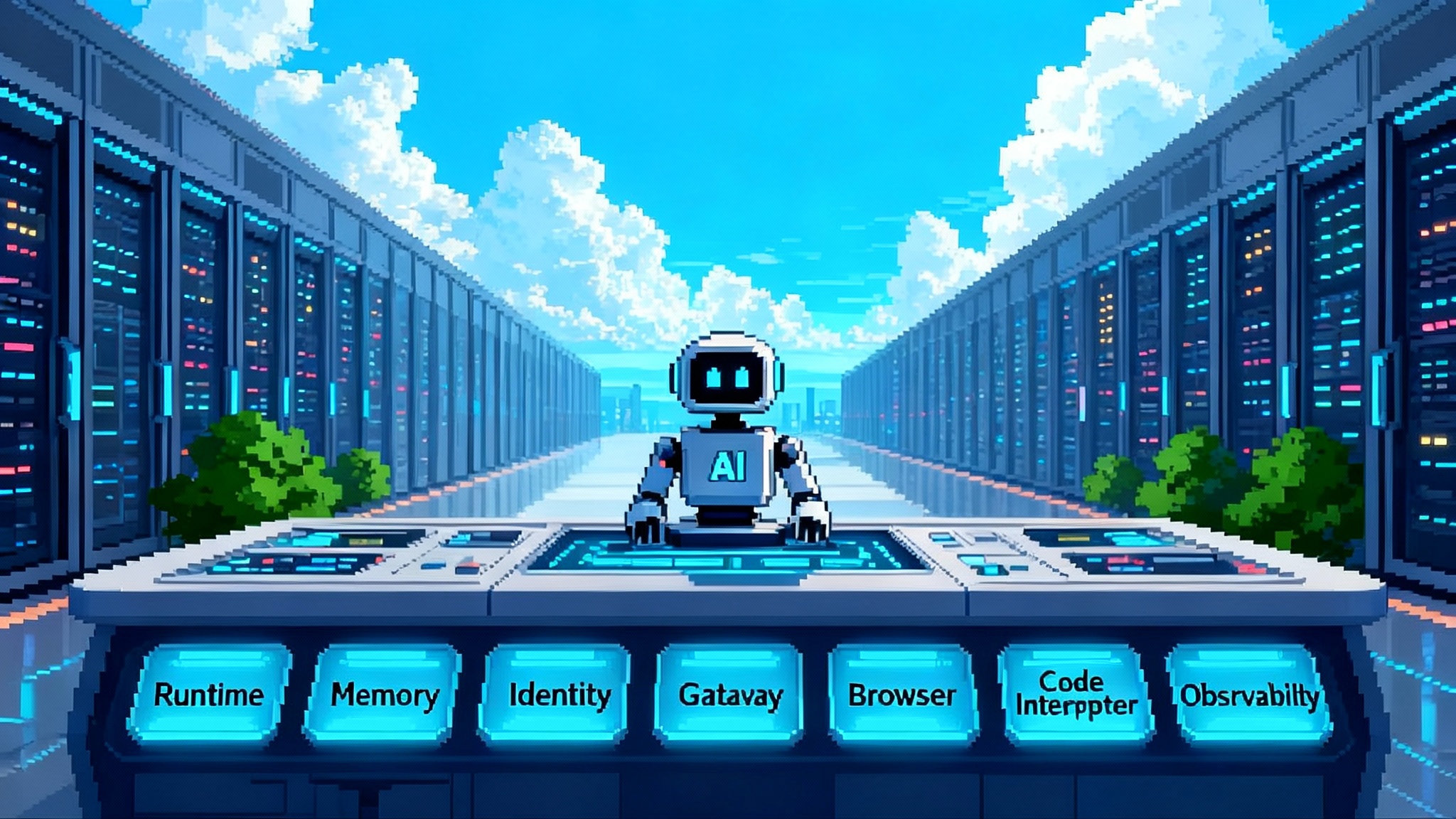
The pitch in one paragraph
Local agents are great for demos. They struggle when the real work begins. Laptops sleep, tokens leak, and background jobs fail in the night. Cloudflare’s remote Model Context Protocol servers flip that story. By putting your MCP tools and agents on a global edge runtime, you get identity that maps to real users and teams, per-user and per-tenant state, and durable execution that survives restarts. The result is less operational drag, safer permissions, and agent actions that scale with internet traffic.
What Remote MCP actually is
Remote MCP is a deployment model where your MCP servers run close to users on Cloudflare’s network rather than inside a developer’s shell. The agent still speaks MCP, but its tools and capabilities live in a managed, globally distributed runtime. Think of it as moving from a local toolbox to a shared, governed service plane.
At a high level, Remote MCP bundles three primitives that teams normally stitch together by hand:
- Identity delegation that lets an agent call tools on behalf of a user or workspace, with scope and lifetime controls.
- Per-user and per-tenant state so tools can read and write memory without trampling on other tenants.
- Durable execution so long running tasks keep going if a single instance goes away, and so steps can be resumed and audited.
If you already build on Cloudflare Workers, these ideas will feel familiar. Workers give you a highly available serverless fabric, and Remote MCP layers the agent protocol and control surfaces on top. For background on the runtime itself, see the Cloudflare Workers documentation.
Why this matters now
Enterprises want agents that can take real actions without fragile desktop setups. Security leaders want explicit scopes, traceable access, and revocation. Platform teams want paved roads for storage, scheduling, and network boundaries. Remote MCP gives you these building blocks without forcing a rewrite of your agent logic. You keep the MCP contract and upgrade the place where it runs.
The three primitives in practice
1) Identity delegation
Agents rarely act as themselves. They act for a person or an application. Remote MCP treats identity as a first class input. A session maps to a specific user or service principal. That identity flows through tool calls so downstream systems can enforce permission checks. You can issue short lived credentials for a risky task, or long lived tokens for back office jobs, with explicit scope lists rather than broad keys.
Good practice is to keep the blast radius small. For sensitive tools such as finance, require a privileged scope and a separate approval step. For read only tools such as search, allow wider use with shorter lifetimes.
2) Per-user state
Agents improve when they remember. Remote MCP supports scoped storage so each user and tenant has an isolated slice of memory. This could hold preferences, recent conversations, cached embeddings, or partial results between steps. Isolation means one tenant’s memory cannot leak into another’s workflow. It also simplifies data retention rules because you can tag and purge at the right granularity.
3) Durable execution
Many useful tasks are not single shot completions. They wait on webhooks, crawl a large site, or fan out to dozens of systems. Durable execution keeps these tasks alive and resumable. A step can checkpoint its progress, store intermediate artifacts, and retry when a dependency recovers. If an instance restarts during a deployment, the job does not vanish. Durable behavior is the difference between assistant as novelty and assistant as operations.
A request lifecycle, end to end
Here is how a typical call flows when an end user asks an agent to book travel under company rules:
- The client initiates a chat with a signed session that ties to the user’s identity and scopes.
- The agent plans a tool sequence: pull policy, check budget, search flights, hold options, request approval, complete purchase.
- Each tool call runs in a Remote MCP server close to the user for low latency, with state writes tagged to that user and tenant.
- Steps that require waiting, such as manager approval, park in durable queues with a time limit and a reminder.
- Audit logs capture who asked, what scopes were used, what external calls were made, and which data was touched.
- If the user cancels, the workflow halts, releases holds, and writes a final record for compliance.
Reference patterns you can copy
Pattern 1: Per user copilot with safe write paths
- Tool set: read email, summarize documents, draft replies, create calendar holds.
- Writes are gated through a policy tool that validates sender, destination, and content class before any send action.
- Memory keeps a rolling summary and a list of sensitive correspondents to protect.
Pattern 2: Multi tenant back office automations
- Tenants bring their own connectors and secrets.
- Each tenant gets a namespace for storage and logs that can be exported upon request.
- A single MCP server hosts tools for all tenants, but every call includes a tenant key and per tenant rate limit.
Pattern 3: Research agent with human in the loop checkpoints
- The agent crawls sources, extracts facts, and drafts a report.
- At checkpoints it pings a reviewer, waits for feedback, then continues to the next section.
- Every step and source is recorded for later verification.
For teams productizing agent capabilities, consider how an ops layer for production agents aligns with this model, as discussed in our coverage of ops layer for production agents.
Migration playbook from local to remote
You can move to Remote MCP without a rewrite. Treat it as a packaging and policy exercise.
- Inventory tools. List all MCP tools, their inputs, outputs, required secrets, read and write surfaces, and expected runtimes.
- Define scopes. For each tool, define read and write scopes that match business risk. Keep scopes small and explicit.
- Harden secrets. Replace local environment variables with store backed secrets. Rotate keys and remove any hardcoded tokens from scripts.
- Map state. Decide which memories are per user, per tenant, or global. Create namespaced storage keys and retention rules.
- Add checkpoints. For long tasks, add save points and idempotent operations so retries do not duplicate work.
- Instrument. Emit traces and metrics by tool name, latency percentile, error class, and downstream service.
- Throttle and retry. Add backoff policies and rate limits per tool. Prefer small retries over heavy single attempts.
- Shadow traffic. Run your remote instance in parallel with local usage. Compare outputs and latencies before switching default.
- Flip the routing. Move clients to remote by default, keep local as a fallback for a short period.
- Close the loop. Capture user feedback and failure modes, then tighten scopes and timeouts.
If you use SDKs to structure tool calls and plans, approaches like the way the Agent SDK make agents dependable can help with retries and evaluation. See our analysis on Agent SDK make agents dependable.
Security, governance, and compliance
Security for agents is not only about secrets. It is about controlling what an assistant can do for whom, under what conditions, and with what audit trail. Remote MCP gives you control points at each layer.
- Identity and scopes. Require proof of identity on every call. Keep scopes granular. Expire scopes after the shortest useful period.
- Approval workflows. For destructive or costly actions, build a secondary approval tool. The agent requests permission and waits.
- Data boundaries. Write and read only within a tenant and user namespace. Avoid global caches for sensitive content.
- Network policy. Allowlist egress domains for tools that fetch data. Reject calls to unknown hosts by default.
- Audit logging. Record tool name, parameters, scope, user or service principal, target systems, and data locations.
- Retention and deletion. Set per tenant retention. Offer export and purge functions so customers can meet obligations.
For organizations building marketplaces of tools, governance must scale with the catalog. We cover blueprint patterns in MCP marketplace patterns.
Observability and reliability at the edge
You cannot improve what you cannot see. Treat your MCP servers like production microservices.
- Structured logs. Emit machine readable entries with request id, session id, tool, latency, and error code.
- Tracing. Link the agent plan to the tool calls so you can follow a request through its steps.
- SLOs. Define a target availability and p95 latency per tool. Alert on budget burn, not only on single spikes.
- Backpressure. Use queues and rate limits to protect fragile downstream systems. Drop work that is no longer relevant.
- Idempotency keys. Ensure retries do not double charge cards or submit duplicate tickets.
- Chaos drills. Kill a worker mid task and prove that durable execution finishes safely.
Performance and cost
Edge execution shines when tools depend on public APIs or user traffic concentrated in certain geographies. Short lived, stateless calls are cheap and fast. Long crawls and heavy compute need careful design. A few practical tips:
- Warm up paths. Keep hot tools alive by pacing small background requests.
- Batch where safe. Group small read operations to reduce chatter, but do not batch writes that must be individually auditable.
- Cache immutable results. Cache schema fetches and static lists with modest TTLs.
- Place compute near data. If a tool must read a large private dataset, consider a regional variant of the MCP server.
- Measure p95, not average. Users feel tail latency. Track it per tool and per region.
How Remote MCP fits in the ecosystem
Remote MCP is not the only path to production agents. It is a compatible runtime for MCP flavored tooling that excels at global distribution and safe, durable execution. You can blend it with other stacks. For example, a company that adopted an ops layer for production agents might route certain tools to Remote MCP to improve latency near end users. Teams investing in SDK driven plans and evaluations, like those discussed in Agent SDK make agents dependable, can keep those patterns while moving the tool plane to the edge.
A worked example: from laptop agent to shared service
Imagine you have a local research agent that reads a batch of URLs, extracts company facts, and produces a single page brief. It uses three MCP tools: fetch, extract, and write to a team wiki.
- Scopes and identity. You create three scopes: fetch.read, extract.process, wiki.write. Only the last scope can change state in external systems. The agent requests all three but they can be granted separately.
- Storage design. You store raw pages in a per user bucket, extracted facts in a per tenant store, and final briefs in the wiki under a team space.
- Durable steps. Each URL becomes a task that can pause and resume. You checkpoint after fetch, after extract, and after wiki write.
- Observability. You emit one trace per URL with child spans for fetch and extract. The parent span covers the entire brief.
- Policy guard. The wiki tool checks for red flags in the draft such as unverified numbers. If present, it routes to human review.
- Shadow run. For a week you run local and remote in parallel, compare outputs for correctness, then switch traffic.
When complete, nothing in your agent logic changed. The environment around it grew safer, more reliable, and easier to scale.
Developer ergonomics
Developers want paved roads that feel familiar. Remote MCP leans on standard HTTP semantics and the MCP contract, so it fits into existing agent frameworks. If you run your tools as small web handlers today, the move is mostly packaging and policy. If you built tool logic tightly coupled to a desktop environment, use this migration as a chance to separate concerns: core logic, IO adapters, and policy wrappers.
For a deeper look at the contract itself, read the Model Context Protocol spec. It explains how servers expose capabilities, how clients negotiate, and how tool calls are structured.
Frequently asked questions
How do I keep private data safe if the runtime is at the edge.
Scope secrets per tenant and do not mix data in shared caches. Encrypt at rest and in transit. Use short lived credentials. Keep allowlists tight.
Can I run custom binaries as tools.
Yes, behind a thin HTTP adapter. Keep them small and stateless where possible. For heavier jobs, offload long compute to a dedicated service and call it from the tool so your edge process stays responsive.
What about cold starts.
Keep the critical path small and warm. Avoid heavy imports during startup. Preload configuration in a shared read only object when possible.
How do I test locally.
Use the same MCP servers with an alternate config that points to local mocks for storage and network. Run the same traces and metrics locally so you can validate parity.
A simple readiness checklist
- Scopes are written, reviewed, and mapped to tools.
- All tools emit structured logs and traces.
- Secrets are rotated and removed from code.
- Storage namespaces are defined by tenant and user.
- Idempotency keys exist for every write.
- Error classes and retry policies are consistent.
- Approval flow exists for risky actions.
- Shadow run plan is ready with success criteria.
What success looks like
After the move to Remote MCP, teams report fewer one off fixes and more predictable behavior. On call rotations shrink. Approvals and audits stop being a scramble. New tools publish with a standard checklist rather than bespoke risk reviews. Most importantly, end users get faster, safer agents that feel like a product rather than a project.
Final takeaway
Remote MCP makes the edge a first class home for AI agents. It brings identity you can reason about, memory you can govern, and execution you can trust to finish the job. If your agents still live on laptops, your next release should make them residents of the network instead. Start with the smallest useful tool, prove the guardrails, then promote the rest. The gap between demo and production closes when the runtime pulls its weight.