Receipts Become a Primitive: The AI Signature Layer Arrives
Europe’s new push to label AI-made media and product moves like SynthID and one-click Content Credentials point to a new default: content ships with receipts. Here is why provenance becomes product DNA and how to build for it now.

The week receipts went from nice to must
On November 5, 2025, the European Commission kicked off a process to draft a code of practice for marking and labeling AI generated content. The move gives the industry a practical path to meet transparency duties in the European Union’s Artificial Intelligence Act. More importantly, it signals something bigger: provenance is becoming part of the default stack for digital media. In plain terms, the internet is getting a signature layer. Providers and deployers will not just create or host media. They will sign it and show their work. That becomes the new baseline.
You can read the Commission’s own description of the kickoff and process in its post on the Commission code of practice overview. It sets the stage for machine readable labels and disclosures at scale, with a concrete drafting window rather than vague aspirations. While voluntary, the code is designed to plug directly into obligations that already exist under the AI Act.
Meanwhile, product teams moved. In 2025, Google introduced SynthID Detector, a portal that helps identify content made with Google models. Cloudflare rolled out one click Content Credentials for images that preserve edit history as those assets move across the network. Combine these with the earlier spread of C2PA support across cameras, creative tools, and content workflows, and a pattern comes into focus. The signature layer is not one product or one law. It is convergence.
Receipts, explained in under a minute
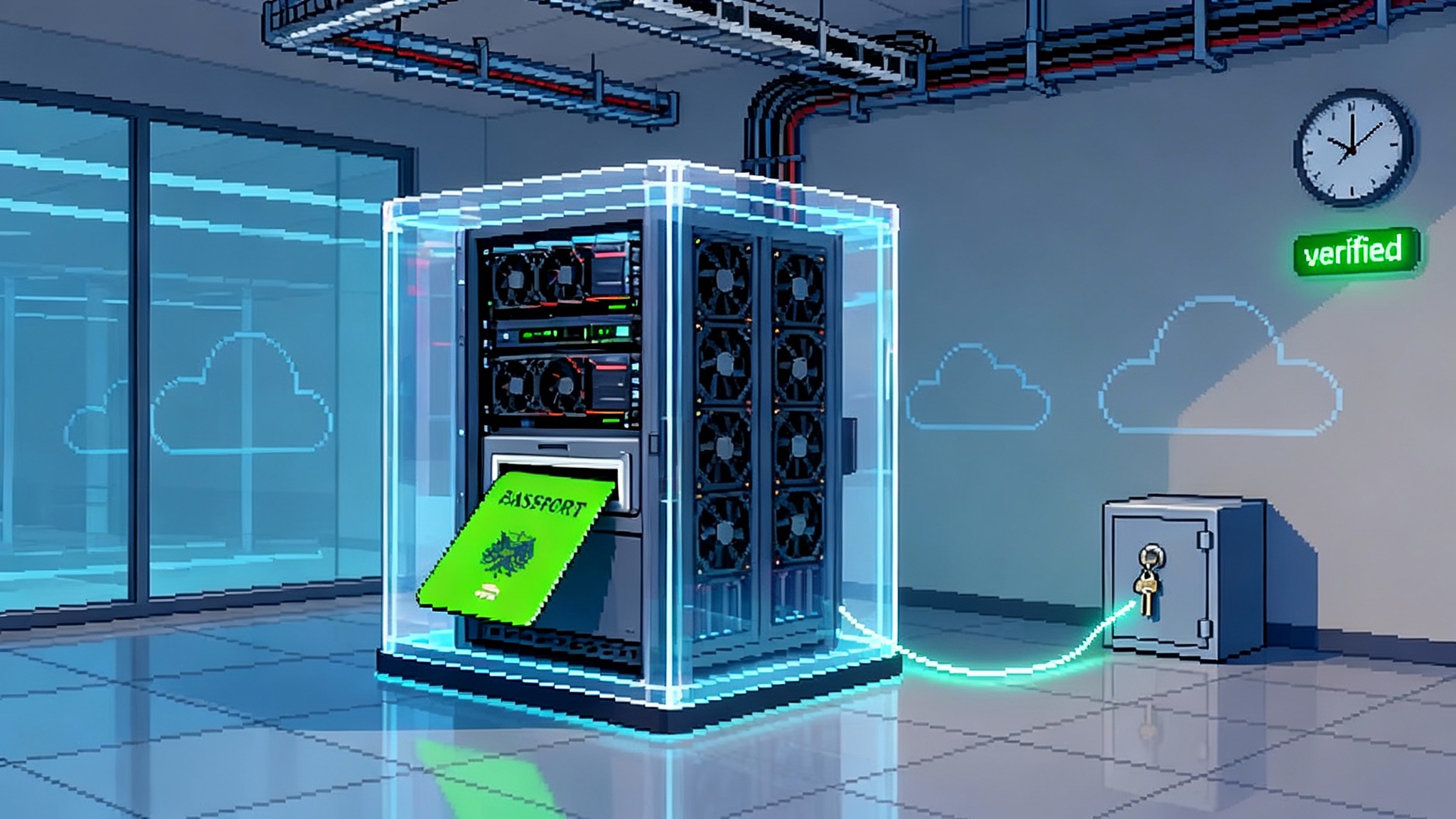
Think of a digital receipt as a media passport. It travels with your image, video, or audio and lists how it was created and changed. Who stamped the passport. Which countries it visited. What dates. In more technical terms, it is a chain of custody record bound to the file with cryptographic signatures or robust metadata. You can verify the passport at any checkpoint. If you trust the stamp issuer and the signature, you can trust the story the passport tells.
Receipts beat eyeballing for the same reason bank statements beat a pile of cash on a desk. You do not have to guess how the money got there. You have a record. As generative tools make convincing fakes cheap, the value of a portable, verifiable record increases. Watermarks can help but are often fragile under edits and compression. Receipts focus on visible accountability.
For a deeper dive into infrastructure level trust, see how attested AI becomes default. Receipts for content and attestations for compute are two halves of the same idea: verifiable origin.
Why November 5 changed the tone
The Commission’s move did not invent provenance. It made provenance operational. Providers now have a reference for what to build and how to show compliance. Deployers understand what is expected when they publish synthetic content on topics of public interest. Regulators get a constructive lane to nudge the field without freezing it.
The code of practice is voluntary, but it dovetails with obligations that already exist under the Artificial Intelligence Act. That is the part product teams should note. Voluntary code, real obligations. The code describes practical paths to meet them. The implication is simple. If you ship content without signatures or labels, you will swim upstream against regulatory current and platform defaults.
From feature to primitive: how provenance reshapes UX
Provenance by default changes interface design in concrete and predictable ways:
- Signed headers. News sites and social platforms show a small badge near media. Tap or click to reveal the media passport. The badge indicates that the media carries a verified signature from a recognized issuer.
- First class inspect. Every image viewer, video player, and audio app gets a persistent inspect affordance. Users learn to check context before they share, much like they learned to expand previews before clicking.
- Autofill credits. Image editors preserve creator, tool, and edit steps. Resizes, crops, and color tweaks become explicit entries in the passport. Attribution is embedded rather than pasted.
- Trust weighted feeds. Ranking algorithms favor content with verifiable provenance when topics are sensitive or when accounts are new. This lowers the blast radius of new hoaxes and rewards creators who sign.
- Share with proof. When users repost, platforms keep the passport intact, including edits or overlays the user adds. This builds a traceable story of a meme or a news clip as it morphs across the web.
None of this requires users to become cryptographers. The design work looks like safety labels, padlock icons, and nutrition panels. The hard part happens under the hood.
Under the hood: keys, standards, and survivability
Two technical commitments make the signature layer useful.
- Strong keys. Signatures are only as good as the custody of private keys. Publishers and toolmakers need managed keys or hardware backed storage. Rotations must be simple. Revocation must be visible.
- Durable metadata. Credentials must survive compression, resizing, and format conversion. That is why standards like C2PA matter. They define a way to bind claims and track edits as derivatives are produced.
Cloud delivery helps because provenance has to live at the edges. Cloudflare’s one click Content Credentials meets creators where they already upload, resize, and serve images. The result is less ceremony at the source and more consistent receipts downstream. Google’s SynthID Detector complements this by giving a place to verify watermarks from its own tools. One preserves receipts. The other tests for hidden marks.
The compliance driver: training lineage goes public
There is a parallel shift on the model side. General purpose model providers in the European Union are expected to publish summaries of training content sources, list major datasets, and explain how the data was obtained and filtered. The Commission provides guidance and a template that shape these disclosures. This is not trivia. It is provenance for the model itself.
Read the Commission’s overview of the new obligations and the template on its portal in GPAI obligations and template. The effect is a forcing function. If models must disclose their training lineages, downstream products have to reconcile their content receipts with the training receipts.
Consider a simple example. Your agent cites a passage from a knowledge base, and that base contains scraped material later flagged by rights holders. If your chain of custody is strong, you can trace back and replace the source, or at least notify users and downstream partners. The web gets remediation loops rather than one way flows.
If you want the policy backdrop on licensed data and incentives, read our take on the consent layer for training. Training lineage is not just compliance. It is a product input.
The agent era needs receipts most of all
Autonomous agents fail gracefully only if they can show their homework. An agent that bought the wrong part, booked the wrong flight, or sent the wrong email is less scary if you can inspect its sources, prompts, model versions, and decision thresholds. Receipts are that audit trail.
Three shifts will make or break agent trust:
- Source citing as a first class action. Agents attach citations that are clickable and inspectable. This can include intermediate steps if they materially affect the output. Instead of a brittle wall of logs, expect a compact, structured report that aligns with a media passport: inputs, tools called, outputs, and signatures.
- Chain of custody in storage and transport. Each handoff between tools records a signed event. File storage, vector stores, and message buses add provenance fields and checks. When an agent hands an image to a layout tool, the receipt grows by one line. When it hands a quote to a publishing system, the receipt gains a source hash and a time.
- Watermark awareness. Receipts work with watermarking rather than replace it. Detectors flag probable synthetic regions, and receipts declare synthetic steps. The two together make tampering and omission expensive and obvious.
We have written about how firms are evolving into run times in Agent OS turns the firm. Agents need surfaces to show receipts as naturally as they show progress or cost. Expect the receipt view to become a first class screen in agent UX.
Product playbook: what to build next
If you ship content or build with models, your road map for the next three quarters likely includes the following. Treat it as a checklist.
- Sign on ingest. When you accept media uploads, assign a provenance profile and sign the original. Store a compact receipt alongside the file. Do not wait for publish time. This ensures early edits are tracked.
- Preserve and display. Ensure all transforms carry forward credentials. Add a visible inspect control in your viewer or player. Default to showing the receipt when content goes viral or when a user flags a post.
- Rotate and revoke. Automate key rotation and display revocation status in the passport. If a signing key is compromised, users should see that the chain has a break.
- Train with receipts. If you operate a model, maintain a training lineage that maps sources to model versions. Surface that lineage at the model card level so downstream integrators can inherit it.
- Score for trust. Add a trust score that feeds ranking and monetization. Receipts that pass verification, recent signatures, and known issuers increase rank. Missing or tampered credentials reduce distribution. Be explicit about these rules in your policy docs.
- Prepare for audits. Your compliance team will need a single report that shows how your system marks AI content, how you meet disclosure requirements, and how users can verify. Build that report format now rather than scrambling later.
A sample architecture
A practical stack for receipts can be incremental and boring by design:
- Issuance service. A backend service that signs originals on ingest, attaches C2PA claims, and writes a short receipt document to object storage.
- Verification library. A client library in web and mobile that reads receipts, checks signatures against a whitelist, and renders a simple passport UI.
- Key management. A dedicated service that handles key generation, storage, rotation, and revocation. Integrate with a hardware security module or managed KMS.
- Policy engine. A ranking component that turns verification results into distribution levers. This is where trust scores connect to feeds and ad placement.
- Observability. A dashboard that tracks receipt coverage, verification failures, issuer health, and revocation events. Treat it like uptime for provenance.
Distribution economics shift toward signed media
Search, social, and ad networks optimize for signals that reduce risk and increase relevance. Receipts do both. Expect a measurable advantage for signed content in at least three places:
- Sensitive topics. Health, elections, finance, and breaking news will see stricter boosts for signed media. Unsigned media will still exist, but its reach and recommended surfaces will narrow.
- New accounts. Provenance acts as borrowed reputation. New creators who sign will overcome cold start penalties faster because their content carries checkable history.
- Brand safety. Advertisers will pay more to appear next to content with verifiable origin. Expect inventory tiers based on provenance integrity, with clear price differences.
If you run a marketplace or a network, make this shift tangible. Publish a policy that states how provenance affects relevance. Show creators a preview of how their distribution score changes when they add signatures. Turn trust into a dial they can see.
Beware the tricky edges
Provenance is not a magic shield. There are challenges that product teams need to solve with clear policies and technical guardrails.
- Key sprawl. If every tool issues signatures, users will juggle dozens of keys. Solve this with managed identity for tools and organizations, plus delegated signing for trusted third parties.
- Deep copy problems. Screenshots and screen recordings can strip credentials. Build detectors that warn viewers when credentials are missing for content types that usually carry them. Offer a way to request the original from the publisher.
- Partial receipts. Not every step will be recorded. Your UI must show what is known and what is not, without implying false certainty. Make absence explicit.
- Adversarial edits. Attackers will try to poison or confuse provenance. Validation must be strict. Keep a short whitelist of trusted issuers at launch and expand carefully.
- Privacy and safety balance. Receipts should not leak location, identities, or internal tool names. Use scoped claims and redact with intention. Show only what is needed to verify origin and edits.
What it means for creators, publishers, and model builders
- For creators. Start signing today. Use tools that preserve credentials through export and upload. If your platform does not preserve credentials on resize or crop, file a ticket and tell your audience. Being early will raise your distribution and your value to partners.
- For publishers. Require signed assets from freelancers and agencies. Add provenance checks to your CMS on ingest. Reward desk editors who fix broken chains before publish. Track how often provenance reduces corrections or takedowns.
- For model builders. Publish training lineages with clear lists of source types, major datasets, and filters. Provide a remediation path for rights holders. Invest in a small, public facing transparency portal that makes those summaries easy to navigate.
- For advertisers. Ask for provenance tiers in buys. Pay a bonus for signed inventory in categories where risk is high. Track performance uplift by tier to justify the spend.
A healthier question for the web
The web has been missing a universal spell that says this is where this came from. November 5 did not conjure the spell, but it made it part of core memory. As SynthID Detector and one click Content Credentials become default settings rather than advanced options, users will stop asking whether something is real and start asking what happened to it along the way.
That is a better question. It invites nuance. It aligns incentives. It favors craft. And it moves us from a culture of guessing to a culture of checking. The signature layer will not erase misinformation, but it will make honesty cheaper and deception harder. That is a good trade for the internet.
The bottom line
Receipts have become a primitive. They are not a feature to toggle. They are a foundation to build on. The next year will be about turning that foundation into habits people can feel: a small badge that earns a click, an inspect view that answers a doubt, a distribution bump that rewards care, and a training summary that makes an abstract model a little less opaque. Teams that build for this reality will not just pass audits. They will win users who care about what they are seeing.
If you are planning next steps, pair receipts for content with compute attestation. Start with issuance on ingest, durable metadata, and a clear inspect surface. Tie verification to ranking. Publish your policy. Then let creators and users see trust become a visible, working part of your product.