Agent OS Arrives: The Firm Turns Into a Runtime
Enterprise agents are moving from chat to operating system. Builders, connectors, evaluation, and governance turn org charts into executable workflows with budgets, SLAs, and audit trails. Here is the new playbook.
The week the interface disappeared
In October and November 2025, something subtle but historic happened. Chat boxes stopped being the center of the story. A wave of releases from major vendors placed the emphasis not on one clever assistant but on the stack that makes many assistants reliable, accountable, and fit for work. With launches like OpenAI’s AgentKit, GitHub’s Agent HQ, Salesforce’s Agentforce 360, and Databricks’ Agent Bricks, the tone shifted from fun demos to production railways. The message was simple. You are not deploying a chatbot. You are standing up an operating system for machine colleagues.
The new baseline is an Agent OS, short for Agent Operating System. It consists of four pillars that every announcement seemed to echo in its own language: builders to define capabilities, connectors to enterprise data and tools, evaluation to measure behavior before and after deployment, and governance to keep humans in charge and auditors satisfied. Each pillar is old in isolation. In combination they turn an organization into a runtime.
As the UI becomes the API, the chat window is no longer the product. It is one of many triggers in a system that clicks, schedules, files, and settles work across the firm.
From chatty helpers to machine colleagues
For a decade we treated assistants as a thin conversational layer on top of search and scripts. The chat interface was the product. It was polite, it was often helpful, and it could be demoed in five minutes. Enterprises learned three hard lessons.
-
Conversations do not equal commitments. A charming answer is not a contract. Work needs deadlines, owners, and recourse.
-
Integrations are everything. Without access to calendars, warehouses, customer records, and code repositories, the best assistant is a spectator.
-
Safety is an ongoing function, not a feature toggle. You cannot bolt on compliance. You need clean logging, reproducibility, and policy that compiles into controls.
The Agent OS responds by treating agents as first class workers. They need onboarding, role definitions, credentials, quality bars, and measurable outcomes. They participate in workflows that have budgets and service levels. They can be paused, reassigned, and redeployed. That is a workplace, not a chat.
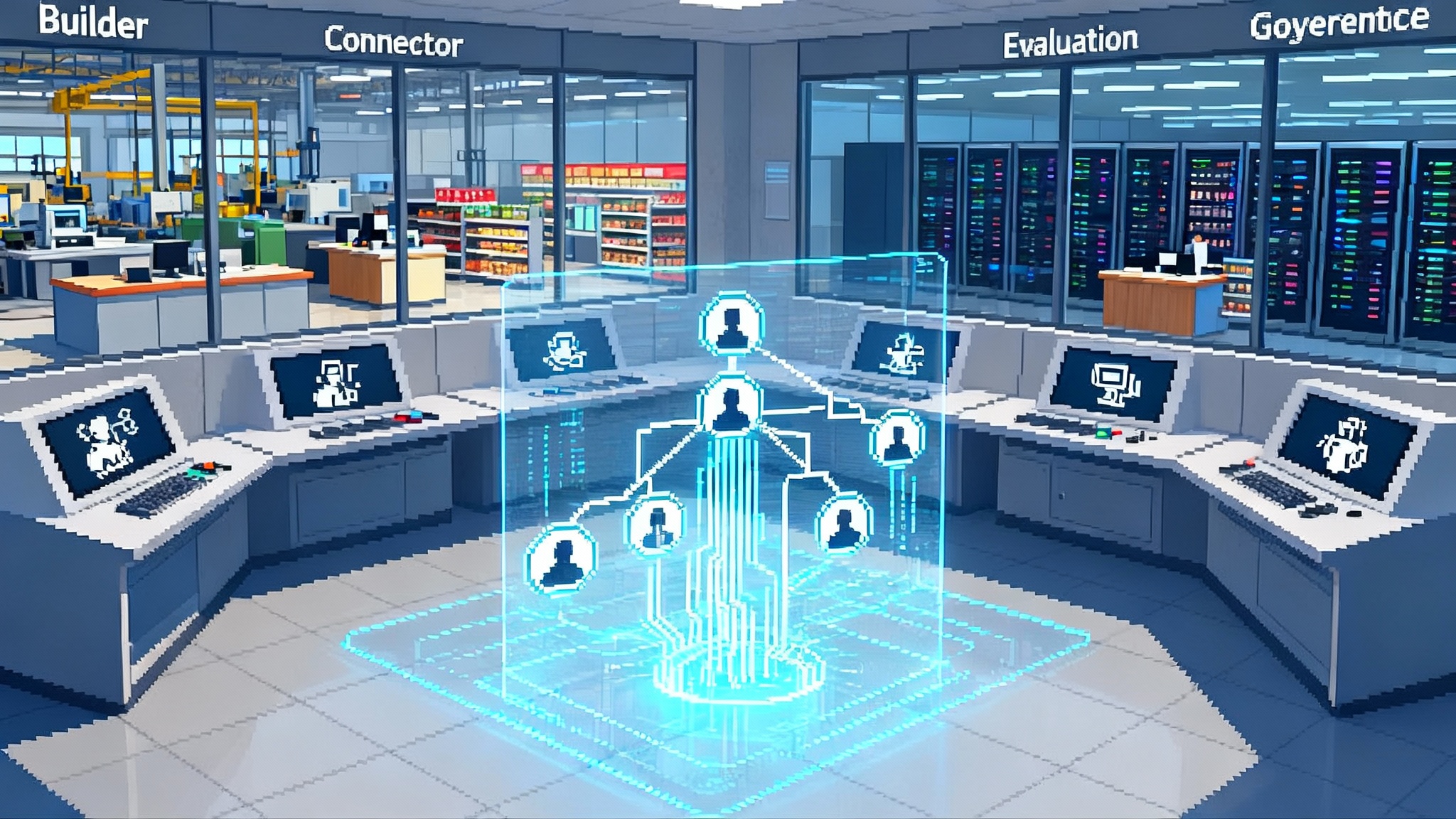
The consolidated agent stack
Think of the Agent OS as four concentric rings that harden as you move outward.
-
Builder ring. This is where teams author agent skills, tool use, and role definitions. It includes templates for common jobs like tier one support, sales prospecting, code refactoring, demand forecasting, and vendor onboarding. You do not hand an agent an open world. You hand it a job description with a catalog of tools and a test bench.
-
Connector ring. This is the adapter layer to calendars, enterprise resource planning, issue trackers, billing, code, and storage. Every connector sets permissions, schemas, and rate limits. The tighter the connector layer, the more predictable the agent becomes.
-
Evaluation ring. Before an agent touches production, it runs through evaluations. These include success criteria on representative tasks, cost and latency budgets, safety probes, red team scenarios, and regression suites. Evaluations continue in production, because environments drift and policies change.
-
Governance ring. This is policy, oversight, and escalation. It includes event logging, data retention, risk scoring, audit trails, and human review flows. Governance is not a formality. It is the interface to legal, security, and finance.
When these rings are present, the conversation interface becomes just one of many controls. You can trigger an agent through a ticket, a webhook, a schedule, or a policy rule. The interface is no longer a chat window. The interface is the firm itself.
Work becomes software
Executives have said for years that every company is a software company. The Agent OS turns that slogan into an architectural fact. The organizational chart becomes an executable workflow. Roles compile into policies. Policies compile into agents, guardrails, and alerts.
Here is a concrete example. Consider a midsize retailer, Harbor Lane, that runs online and in store. In the old world, a stockout triggered a Slack message, a spreadsheet update, and a flurry of manual checks. In the Agent OS world, a replenishment policy watches events from the point of sale, supply chain, and weather data. When the policy detects a risk of stockout, a planning agent creates a restock order, a procurement agent compares supplier terms, and a logistics agent reserves a dock time at the nearest warehouse. A human manager reviews the plan in a control panel and signs off. If the plan exceeds budget, finance rules automatically escalate to a director. The chart of people still exists, but now it is a graph the runtime can execute.
Bots hiring bots
It sounds like satire until you implement it. Once agents have job descriptions, budgets, and evaluation scores, the next step is obvious. Agents can request other agents. A sales operations agent may hire a data enrichment agent for a campaign, specifying a budget, a schema, and a deadline. The request is a structured contract, not a chat.
This is not science fiction. The primitives already exist in software development. Services invoke other services with contracts. The difference now is that the contracts are readable by managers and auditors, not just by engineers. The Agent OS exposes a marketplace inside the enterprise where one team’s best agent can be used by another team with a click. The procurement analog shifts from software licenses to agent subscriptions with service terms.
Contracts and Service Level Agreements between machine principals
If agents can request other agents, they need a way to hold each other accountable. Enter the machine principal. A machine principal is a recognizable, auditable identity with permissions, budgets, and history. Two machine principals can sign a compact that looks a lot like a contract. It has a scope, a cost ceiling, a time bound, and a Service Level Agreement, also called an SLA.
A claims processing example makes this concrete. A health insurer deploys an intake agent that assembles case files, a policy agent that interprets coverage, and a payout agent that executes approved payments. The intake agent contracts the policy agent to deliver an eligibility decision within two minutes with 99 percent coverage of fields. If the policy agent misses the SLA, the intake agent escalates to a human adjuster and logs a missed service count against the principal. Now you can have a real dashboard for agent performance that maps cleanly to operational outcomes.
Observability and insurance replace checkbox compliance
Compliance teams do not want promises. They want evidence. In conventional systems, evidence is slow to collect and even slower to review. The Agent OS flips this by making observability and insurance first class parts of the stack.
-
Observability. Every agent step is an event with a trace identifier, inputs, outputs, prompts, tools invoked, and policy decisions. The log is immutable and queryable. A risk officer can ask, which agents touched Social Security Numbers last week, and get a precise answer in under a minute. Drift in cost, latency, or safety scores triggers alerts.
-
Insurance. If events are granular and reproducible, insurers can price risk. That moves us from blanket exclusions to specific coverage. For example, a warehouse automation agent pool with strong evaluation and rollback receives better terms than an unobserved pool. Insurers will require technical controls such as sandboxing, data minimization, and model isolation in exchange for lower premiums. This ties the cost of risk to the quality of engineering, which is exactly where it belongs.
Evidence is stronger when it is attested. For a view of what that looks like at the infrastructure layer, see how attested AI becomes default. The same mindset now applies at the agent layer through signed artifacts, policy hashes, and verifiable traces.
When Key Performance Indicators become policy
Key Performance Indicators, often shortened to KPIs, have lived on dashboards for decades. In an Agent OS, KPIs compile into policy. If conversion rate drops below target for three hours, the marketing agent reduces bid prices, switches creative, and opens an incident. If margin per shipment falls under threshold on a route, the logistics agent rebalances carriers within contract limits.
This is not a reckless loop. Policy includes bounds, budgets, and an approvals graph. The change history is preserved. Human owners can rehearse policy changes in a simulator before they go live. The important shift is that a KPI is no longer just a number to stare at. It becomes a trigger tied to an action plan the runtime can execute.
Costs and latency will remain dials that teams tune as models evolve. For a deeper look at why this tuning matters, consider how reasoning becomes a dial. The Agent OS makes those dials safe to turn by connecting them to policy guards and budget constraints.
New roles for leaders
The Agent OS does not remove management. It redefines it. The most valuable leaders will do five things very well.
-
Write role charters for machine colleagues. A good charter states the scope, the connectors it may use, the budget, the evaluation gates, and the escalation path. It looks like a one page job description.
-
Commission agent to agent contracts. Leaders should expect their teams to publish their best agents to a catalog with clear service terms. This turns knowledge silos into reusable capabilities.
-
Fund evaluation like uptime. Treat evaluation suites like a production system with owners, on call rotations, and service levels. No suite, no deployment.
-
Make policy testable. Any policy the runtime can change should live in version control with diffs, reviews, and rollbacks. A policy that cannot be tested is a policy that will fail when you need it.
-
Tie financial discipline to observability. Require cost and risk ledgers for each agent. If an agent cannot show its cost per action and risk score by version, it is not ready for scale.
Near term outcomes to expect
Here is what will likely arrive over the next four quarters as this Agent OS paradigm takes hold.
-
Enterprise agent marketplaces. Every large vendor and many enterprises will host internal marketplaces where teams publish agents for others to subscribe to. Listings will include job scope, evaluation scores, cost per task, and incident history. Prices will be transparent for internal chargebacks or for external customers.
-
System and Organization Controls 2 for agents. The familiar audit standard known as System and Organization Controls 2 will evolve rapidly to include agent specific controls. Expect criteria for traceability of prompts and tool calls, separation of duties between builder and reviewer, and provable rollback.
-
The org chart as an executable workflow. Planning tools will render a living diagram of human and machine roles with data flows, budgets, and contracts. Clicking a node will reveal logs, incidents, and policy edits. Board decks will embed live views of this chart because it is the truth source for operations.
-
Insurance riders pegged to evaluation quality. Insurers will add riders that improve premiums if your evaluation coverage exceeds a threshold for critical agents. Coverage will worsen for opaque agents with poor logging.
-
Procurement flipped to outcomes. Instead of buying software seats, companies will buy outcomes. Ten thousand qualified leads per month at a ceiling cost and a service level. Twenty four hour claim turnaround at a measured accuracy and a penalty schedule. The market will speak in metrics rather than feature lists.
A tale of two deployments
To see the stakes, compare two real world styled patterns.
-
Pattern A: Chatbot first. A support team deploys a web chat assistant that answers frequently asked questions. It connects to the knowledge base and logs transcripts. It reduces email volume by thirty percent for three months. Then complexity rises, quality drifts, and incidents stack up. The team pauses the pilot.
-
Pattern B: Runtime first. The same team drafts a support charter with scope, connectors to ticketing and billing, and a budget. They write an evaluation suite for the top fifty intents and a red team set for policy edge cases. They publish a contract for a handoff agent that schedules callbacks. They stand up observability with per intent metrics and error codes. The web chat is just one trigger. After six months, the team has a stable queue time, a predictable cost per resolution, and insurance that covers the automation layer. The pilot scales.
The difference is not the language model. It is the operating system around it.
What to build first
Leaders ask where to start. Pick two domains.
-
Claims that are already structured. Invoices, purchase orders, expense approvals, returns. These are governed by clear rules and have existing data quality checks. They are perfect for agent contracts with tight Service Level Agreements.
-
Workflows with human bottlenecks but predictable steps. Vendor onboarding, new hire provisioning, campaign setup, release notes. These benefit from a builder ring with templates and a strong evaluation suite.
In both cases, assign a human owner, write a one page role charter, define the connectors, and set a small budget with a hard stop. Build the evaluation suite first. Only then publish the agent to the marketplace and invoke it through a policy trigger, not a chat box.
What could go wrong and how to prepare
Two failure modes are common.
-
Quiet drift. Agents slowly deviate from expectations as data or tools change. Countermeasure. Continuous evaluation and versioned policy. Alert on cost or accuracy drift beyond bounds. Require weekly reports that include deltas from last version.
-
Permission creep. Agents accumulate access because it is convenient. Countermeasure. Role based credentials with time limits, explicit approval on scope changes, and a quarterly review that revokes unused permissions. Machine principals must be treated like employees with joiner, mover, leaver processes.
Both failures are cultural as much as technical. The fix is to own the Agent OS as a shared discipline across engineering, operations, risk, and finance.
The broader market shift
The arrival of an Agent OS will change how software is sold and valued. Vendors will compete on connectors, evaluation coverage, and governance depth more than on single model performance. The most valuable companies will be those that make other companies safe and fast at using agents. That includes cloud platforms, observability specialists, and insurers who can price risk responsibly. System integrators will package catalogs of domain proven agents as accelerators. Procurement will favor verifiable outcomes over feature checklists.
Developers will spend less time babysitting prompts and more time writing contracts and tests. Product managers will think in service lines and policies rather than traditional roadmaps. Security teams will get the continuous traceability they have wanted for years. Finance will see a true marginal cost per task with levers to tune it.
For leaders thinking about infrastructure and constraints, do not forget the physical world. The capacity to run agents at scale still depends on energy and hardware. See how grid limits act as a throttle in The Grid Is Gatekeeper. That reality shapes rollout plans and risk models.
The firm as a runtime
Physics has a concept called the phase change. Water turns into ice not because it becomes more watery but because the structure rearranges. Organizations are at a similar point. The components are known. The structure is changing. The chat era gave us a taste of what agents can do. The Agent OS era makes them dependable, auditable, and insurable. It lets us hire machine colleagues with clarity and hold them to our standards.
When your org chart renders as a living workflow, when Key Performance Indicators compile into policy, when agents can contract with each other and publish their service history, the company stops being a static diagram. It becomes a program. That does not make people less important. It makes our intent executable. The firms that learn to write that intent crisply will move faster with less risk. The rest will keep typing into chat boxes and wonder why the results are uneven.
The operating system arrived quietly and then all at once. The next step is to treat it like what it is. A runtime for the business.